Source: Resonant News
Domino’s India Data Breach is one of the most scandalous data breaches of all time, in India. People with malafide intentions can easily misuse that data and can pose life threatening dangers to individual users, as well as groups of people.
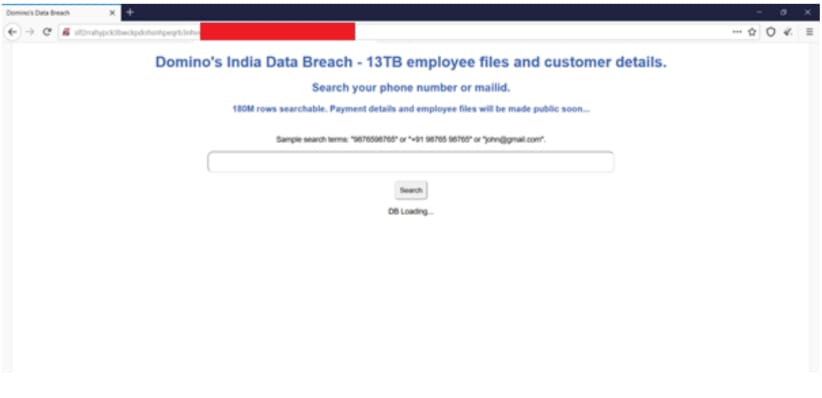
Phone numbers, addresses, GPS Location, email addresses and order amounts of Domino’s users leaked on the internet on May 21, 2021.
A certain link on the dark web is being circulated in the IT circles as well as the criminal ones. This link opens up a webpage which is allowing users to put in any number or email which would render private data results of the Domino’s users
Source: Resonant News
Domino’s India Data Breach is one of the most scandalous data breaches of all time, in India. People with malafide intentions can easily misuse that data and can pose life threatening dangers to individual users, as well as groups of people.
Phone numbers, addresses, GPS Location, email addresses and order amounts of Domino’s users leaked on the internet on May 21, 2021.
A certain link on the dark web is being circulated in the IT circles as well as the criminal ones. This link opens up a webpage which is allowing users to put in any number or email which would render private data results of the Domino’s users
Mobile Number, Email, order amount and details, addresses where the orders were received, and the coordinates of the location. Currently, the payment details are not made public by the hacker but he/she claims to do that soon.
So, while you are reading this, some technologically erudite stalker must be out there collecting the addresses of you and others like you who have used Domino’s in the past. If you are reading this and have used Domino’s, your data is out in the open, just waiting for some malicious person to use it.
There have been several accounts of men and women who have started receiving promotional messages from the past 1-2 days and are feeling uncomfortable already.
The 13 Terabytes of data is available for being sold and the hacker has provided their email ID to be contacted for the same purpose.
How can this data on an individual level be misused?
A person with a criminal mindset, especially stalkers, can access this data and collect the address of the target.
If someone has your number, they can look up the database and find your address. They might show up on your doorstep or follow you. Hitmen can buy this data and keep it in their database. Endless opportunities can be derived out of this data.
The list of addresses where Domino’s delivered for the particular consumer would also be mentioned in that list. This would reveal the location of the person on the particular days. This would especially hurt the partners who have cheated on their other halves and ordered Domino’s Pizza on their way out.
People have been receiving messages and unknown calls (even international) since this incident.
How can this data be used at wide scale levels?
There are massive big data implications of this data breach. The hacker has now provided their contact details to buy the data.
People who are willing to misuse this 13TB worth of big data have uncountable ways to do so. To begin with, targeted ad marketing agencies have already started accessing this data. Now they are able to figure out their target audience and are targeting advertisements towards them. For example -. This gives an undue advantage to the ones who have access to this illegally obtained data. People who are willing to misuse this 13TB worth of big data have uncountable ways to do so. To begin with, targeted ad marketing agencies have already started accessing this data. Now they are able to figure out their target audience and are targeting advertisements towards them. For example -. This gives an undue advantage to the ones who have access to this illegally obtained data.
Terrorist organizations, especially the Islamic ones who look for their recruitment targets in Ghettos, Slums and concentrated populations are sorting out the mobile numbers of their ‘at risk’ population on the basis of geolocation. Suppose they know that a certain area in a city is infamous for hosting gangsters, producing criminals or a hub for extremism, they can filter the mobile numbers in the database by dropping the coordinates of locations around them. These numbers can be contacted by them for the purpose of pushing a social engineering manoeuvre for turning them into their proxies, recruits, etc.
Same goes with drug cartels. They can buy this data and then target the ‘at risk’ population directly. They can gauge the economic condition of a user by looking at their total expenditure on Domino’s.
Carders would get the information about the credit and debit card details if the hacker releases that information as well and this data leak would prove out to be a gold mine. These scammers would create a massive wave of carding incidents in the near future. It’s just a matter of time until that happens.
Political parties who will buy this data would also get the list of numbers in their constituency and would easily be able to push an SMS campaign, more efficiently than others. This would put others in a position of disadvantage as they might not have enough resources to access such data.
This data breach is not concerning the users at an individual level but from a threat to democracy to the threat to individual lives, this breach is encompassing everything.
Why did the data breach happen in the first place?
The data breach is the responsibility of the information security officers of Domino’s India (That is Jubilant FoodWorks). Furthermore, the Government of India and the Ministry of Electronics and Information Technology is responsible for not realising the gravity of the situation and delaying the implementation of the Personal Data Protection Bill.
Personal Data Protection Bill India
The Personal Data Protection Bill, 2019 was introduced in Lok Sabha by the Minister of Electronics and Information Technology, Mr. Ravi Shankar Prasad, on December 11, 2019. The Bill seeks to provide for protection of personal data of individuals, and establishes a Data Protection Authority for the same. The Bill also categorised certain personal data as sensitive personal data. This includes financial data, biometric data, caste, religious or political beliefs, etc.
This bill empowers the citizens and makes the data holders accountable. Not just the data being collected by the Indian companies but also the foreign companies which have personal data of Indians are subjected to scrutiny under this bill. Tough offenses have been laid down in this bill and would improve the situation of data privacy in India.
However, the standing committee on the bill has been seeking extension after extension since early 2020, when this should have been passed in the parliament.
Former Dy National Security Advisor’s view on this Data Leak
“Nitin Pandey’s write up on the Domino data leak brings out the potentially dangerous dimensions of its misuse. In a language understandable to common men, he has explained the process which the hackers use to filter the big data for specific misuse that can harm not only individuals but larger segment of populations. The big data collected from the Domino can be used by terrorist outfits for recruitment, by the political parties for publicity, by the commercial firms for promotional campaigns and by stalkers for targeting their victims. He rightly points out that there are number of possibilities. The mobile numbers, e-mails, addresses of delivery can be used to find out coordinates through the process of filtration. The dark side of the cyber space in which anything can be blown out of proportion and out of context within seconds that influences all has been projected very well by Shri Pandey. He has also underlined the urgent need for approval of the Personal Data Protection Bill of 2019 at the earliest. Importantly, Shri Pandey, a known specialist in the field of cyber security and cyber -crime, has very clearly recommended the role of corporates and the steps needed to be taken by individuals for the protection of the personal data. The article deserves attention of all citizens as cyber-space and Internet of Things have become inseparable parts of our lives.” saidDr S D Pradhan, Former Dy. National Security Advisor, Government of India
Corporate Responsibilities
The general practice of information security audits have been adopted by companies but that is solely because of their business interests. Unless legislative reforms like the PDP bill are into place, the corporates would continue to overlook security vulnerabilities in their systems.
Smith Gonsalves, Principal Consultant & Director CyberSmithSECURE said, “It is very important that the senior management in enterprises be able to simplify security risks to the boards and help those organisations understand the ROI on cyber security. It not only protects the privacy of its users but also prevents business shutdowns.”
Airtel recently announced that they would be investing a huge chunk of their new investments in cybersecurity. More such companies are alarmed by this data leak and are hastily working towards establishing more robust cybersecurity measures.
Past incidents of private data leak
Air India, Dr. Lal Pathlabs, MobiKwik, SBI, BigBasket, Unacademy, Upstox, JustDial, DigiLocker etc. are in the list of companies, banks and Government portals which suffered the most recent cybersecurity incidents. While some accept their data leaks, the others outrightly deny them. MobiKwik, for instance, was being speculated for introduction of an IPO later this year and their data leak thus being by the organization.
These leaks pose an immense threat to our right of privacy and a collective threat to our society and nation. It’s high time that the government holds these corporations accountable and passes the Personal Data Protection Bill as soon as possible.
What Cyber Security and Forensic Experts of India say about this Data Breach?
“The leaked database includes details like users’ phone numbers, addresses, and the number of orders they have placed with Domino’s. Malicious users are using this data to spying on people and also see the past locations with date and time. Which is an extremely dangerous and big invasion of privacy. Businesses who are a victim of a data breach today not only are responsible to protect their consumer’s data, but also prevent it from being misused by the cybercriminals as an aftermath of a data breach.” says Harsh Mukeshbhai Joshi, Information Security Group, HDFC Bank.
Gopika Baghel, Cyber Crime Consultant at Chhattisgarh Police said “Due to this breach, privacy and safety of millions of people is compromised mankind safety is an endangered, especially when you are using the internet to carry out important tasks like online banking and sharing your personal details. It can also cause significant economic loss to the business affected and also losses of competitiveness and reputation. Government should intervene and make strict law against these companies for not securing sensitive data of Indian users. Also, regular audit must be done to identify potential gaps in cyber compliance. This will help in building security areas. This audit can consider dynamic nature of the organization as well as how the organization handles information security.”
“Right to privacy is a fundamental right of every Indian as per the Supreme Court of India. It is really unfortunate to see how irresponsible Government of India is about Users’ Data and Privacy. Thanks to Mr Nitin Pandey for highlighting this Data Leak which is need of the hour.” says Mrityunjay Mishra, a Cyber Security and DeepFakes Researcher.
How to protect yourself from such data breaches
Today was Domino’s, tomorrow would be another application, possibly containing more personal data of ourselves. This warrants immediate attention by the authorities, but for the time being, we have to do our parts.
- Always use UPI for payments. This adds additional security of the bank to the transaction. Wallets and saved card information on applications are often subjected to such data leaks.
- Do not overshare your data online.
- Do not unnecessarily permit applications for the permissions which they do not require, may that be messages, call logs, camera permissions, etc.
- Change your passwords from time to time and refrain from saving your card’s information on such applications.
- Backup your data and system regularly.
- Corporates should conduct regular cyber security trainings for their employees and audit their infrastructure.
- Keep your apps, software, plugins and operating system updated to the latest version.
- Keeping a strong and complex password and changing it periodically is a positive development.
- Companies much have a quick breach response plan. Government should make some policies to regulate them.
- Data should be encrypted because in many cases we have seen that encrypted data is like a garbage for cybercriminals especially when they cannot decrypt it.
About the Author:
Nitin Pandey is a renowned Cyber Security, Dark Web, Counter Terrorism Researcher and Cyber Crime Investigator, currently working as a Consultant with State Police. He has experience of more than a decade in Cyber Security Domain. His work and expertise has been acknowledged worldwide.
Twitter/Instagram: @initinpandey